Part two of the Free Press’ examination of information security at The New School. Click here for Part one.
In 2008, software developer St. John Johnson was studying computer science at Sacred Heart University in Fairfield, Connecticut.
At the time, Sacred Heart utilized the network access control system SafeConnect as a means of maintaining and regulating the university’s Internet network. The software, however, piqued Johnson’s curiosity; he wanted to devise a way to test SafeConnect’s prowess and determine what its capabilities were.
Johnson needed only an Internet connection, an Xbox, and a little knowledge of networking to develop a ”bypass” of the SafeConnect installer and find a way onto Sacred Heart’s network unmarked. Not only did Johnson succeed, but he also discovered that it was “painfully obvious” that SafeConnect was designed to “report back — at the minimum — installed software, versions, disk space, [and] network information” from any user’s computer. To Johnson, who now works as a software development engineer for Yahoo! Inc., the program’s capabilities were apparent: whether or not SafeConnect was actually used to access its users’ information, it was certainly able to do so.
In 2010, The New School implemented SafeConnect to regulate its own campus Internet network, replacing a similar software from Cisco Systems. The primary function of the SafeConnect, as well as the Cisco software, is to ensure that proper anti-virus controls are installed on machines using The New School’s network.
“When we looked to replace the Cisco software, we looked to replace it with something that would give us the same functionality,” said Chris Brezil, assistant vice president of information technology at The New School. “One of the main goals is to protect our systems. We’re also protecting your systems.”
SafeConnect, however, has become a point of contention among many in The New School community. Students and faculty have complained of incessant prompts to download the SafeConnect policy key, which appears repeatedly even after the program is already installed on a user’s computer. In 2010, Parsons professor Ted Byfield wrote a 20-page report to the administration on the program’s technical dimensions, outlining concerns with SafeConnect that he found “incompatible with The New School’s history, values and mission.” And others have taken issue with the fact that the university sparingly consulted students and faculty about having to install third-party software onto their personal computers in order to access the New School network.
“If you’re going to have to install software on your computer, [The New School] should spend some time explaining why and reassuring people that it’s not a big deal,” said Nidhi Srinivas, a professor at The New School for Public Engagement. “Neither was done.”
For the second part of our examination of SafeConnect and its implementation at The New School, the Free Press spoke with students, faculty and administrators about the software and concerns over its capabilities. While administrators from the IT department claimed that the program is secure and serves a practical purpose, the response from students and faculty proved altogether more skeptical. It also appears that such reservations have made their way to the highest levels of the administration, with preliminary discussions reevaluating the future of SafeConnect at The New School now underway.
****
Brezil claimed that when The New School was deliberating the implementation of SafeConnect in 2010, the matter was discussed with students, faculty and administrators throughout the university. “Presentations were made for the deans and officers at the university,” he said. “We spoke with the student senate about the move. So there was considerable interaction with a number of people at the university.”
The New School is not alone in its use of SafeConnect. IT departments at universities across the country rely on the system to ensure that computers connected to their campus Internet networks are protected from malicious software and viruses. Brezil noted that this is a key concern for The New School’s own network.
“Any machine on the network can be affected by a virus outbreak,” he said. “Even with proper anti-virus software, the viruses change definitions and things happen so quickly [that] it’s really crucial that up-to-date virus signatures on the machine are there.
When the Florida-based software company Impulse Point first developed SafeConnect, it was marketed as a tool that would combat peer-to-peer file sharing and other forms of web piracy. On The New School’s network, P2P software such as BitTorrents are flagged, though the IT department said SafeConnect was not implemented with the intention of monitoring such activity. Rather, the software was meant to operate as a means of regulating who can access the network and ensuring that antivirus protection is enabled.
David Curry, The New School’s director of information security, confirmed that the university logs basic information on who accesses its network, doing so through the network firewall. He said that the logs are kept for approximately 30 days, allowing The New School to comply with a law enforcement subpoena if necessary. Curry added, however, that “we don’t do any keyword monitoring,” in explaining the extent to which IT keeps tabs on the network.
“It’s not a business that we want to be in, to be able to see who’s looking at what,” Brezil said about the logging of students’ personal information. “It’s not a concern of ours, as long as there is no legal responsibility we’re bound by to do something.”
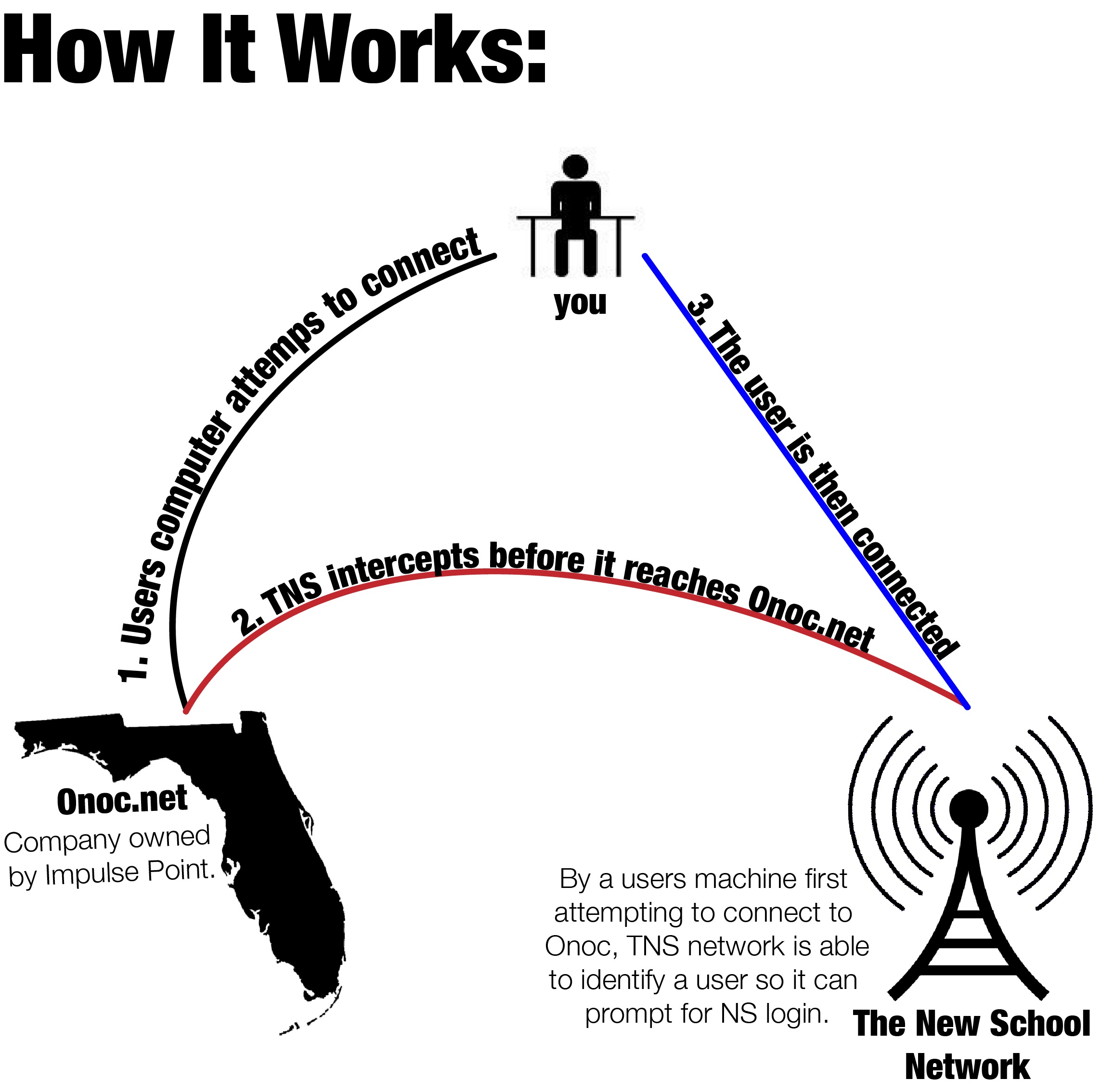
Much of the controversy surrounding the use of SafeConnect stems from a vulnerability that was found in an older version of the software in 2011. The vulnerability allowed for the interception of communication from SafeConnect users. Curry, however, felt the need to clarify exactly what that entailed.
“There is a network address that is built into every SafeConnect client,” he said. “If you look up the network address, it belongs to onoc.net, which is owned by the same people who own Impulse Point. But [users] never actually talk to that address.”
Many New School alumni still have versions of SafeConnect on their computers, including the version that was found to be vulnerable. Curry denied that this posed a problem.
“If you go [online] away from The New School and try to connect to the Internet,” he said, “that address goes down to Florida and then it just falls off the face of the Earth. There’s nothing at that address. That’s why we weren’t concerned about that vulnerability.”
****
Among students and faculty, however, SafeConnect has proven considerably less popular. For many, one particular issue concerns having to install the software multiple times — something that Brezil said has yet to be looked into, but which IT is willing to explore.
“It’s annoying that you have to reconnect each time,” said Parsons freshman Nicole Abesamis when asked about her experience with SafeConnect. “It’s super frustrating when you’re in a hurry, and it’s one more thing you have to put on your computer.”
NSPE professor Nidhi Srinivas expressed his distrust with “software that I have to install again and again. SafeConnect, whenever I use it, forgets my existence though it’s installed.” Srinivas, who served as co-chair on the University Faculty Senate during the 2010-11 academic year, pointed to a report released by the senate’s infrastructure committee at the time. The report questioned software’s cost efficiency, as well as the merits of its continued implementation at The New School.
“I can’t argue, categorically, that [SafeConnect] is the worst issue at our university,” Srinivas said. “But it seems to me really surprising, given how many people dislike it, that the university has not dealt with it. I still don’t see why we need it.”
Recently, however, there is evidence that The New School is reevaluating its commitment to SafeConnect. University Student Senate co-chairs Bronwyn Lewis and Melissa Holmes told the Free Press that they have raised student and faculty concerns regarding the software in recent meetings with President David Van Zandt and Linda Reimer, senior vice president for Student Services. Lewis said that Reimer put her in contact with Shelley Reed, senior vice president of information technology, and that the USS expects to meet with IT in the coming weeks to discuss SafeConnect’s future at the university.
Lewis said that she is “personally in favor of getting rid of [SafeConnect],” describing the software as “an annoyance” and “completely unnecessary.” Though the conversation is still in its preliminary stages, Holmes expressed confidence that “by next school year, there won’t be SafeConnect at The New School.”
In an email to the Free Press, Van Zandt acknowledged student and faculty reservations over SafeConnect, confirming that the administration has “discussed SafeConnect with the University Student Senate and the University Faculty Senate. We are working with a team that has considerable experience in info tech security in academic settings to advise not only on this issue, but The New School’s overall IT portfolio.”
Lewis said that through her discussions with Van Zandt and Reimer, she does believe that the administration is open to discarding the software. “I think that President Van Zandt and Linda Reimer are in favor of improving the student experience,” she said. “It’s a positive thing for the school to get rid of [SafeConnect]. The sooner the better.”
with reporting by Carib Guerra, Katie Bamberger, and Rey Mashayekhi







One response
[…] Are SafeConnect’s Days Numbered? […]